Cyberproof your manufacturing organisation !
Get a headstart in securing your organisation from cyberthreats with hands-on advice share in a recent EIT Manufacturing whitepaper and webinar.
While industry 4.0 with its connected machines, and 5G are bringing many opportunities to improve flexibility, efficiency, and sustainability, these new technologies do not come without a trade-off. Concerns about cybersecurity have made it to the top of the boardroom agenda are there to stay. That’s why EIT Manufacturing cooperated with Cap Gemini Invent to produce a comprehensive whitepaper, and organising a webinar. The webinar and whitepaper offer a comprehensive overview of the type of threats, a decision-making matrix, and some relevant use-cases for inspiration. Both are now available on AGORA, EIT Manufacturing’s Open Innovation platform, in a dedicated Tech & Industry sphere.
Factory 4.0 is a change in both supply chain and the value chain, within and outside the organisation and involving multiple new technologies. But each of these technologies are also a new angle of attack and require a completely new, holistic perspective.
Kary Bheemaiah, CTIO Cap Gemini Invent
More on AGORA, EIT Manufacturing’s Open Innovation Platform
Access the Whitepaper and webinar
The whitepaper was recently presented by Kary Bheemaiah, CTIO Cap Gemini Invent with an introduction by Dr. Kaitai Liang from TU Delft. They were joined on stage by Anmol Singh from Microsoft, and Maxim Kostin from Access Hub to debate related hot topics such as data sovereignty, and data privacy concerns.

Easy to use toolkit to map sources and types of threats.
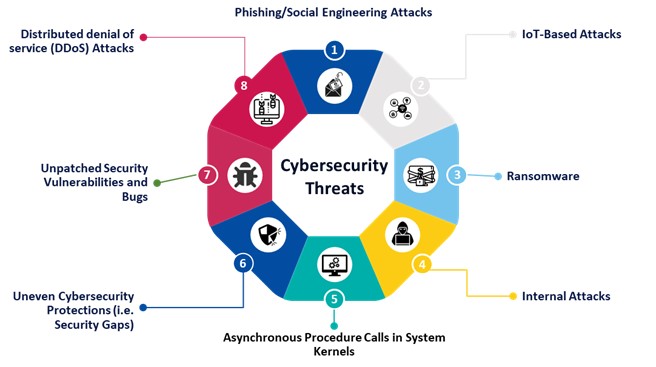
Cyber threats grouped into several categories depending on their source such as: Legal threats, nefarious activities and abuse, eavesdropping, interceptions and hijacking or physical attacks. Moreover, cybersecurity attacks can happen at different stages of the value chain. Thanks to a deep analysis, the team behind the Whitepaper was able to assess severity of various risks and create a Go-No-Go Decision Matrix, identifying critical steps to undertake to quickly get control of the situation.
The image below is describing types of cybersecurity threats:
The next webinar in the Tuesdays from Future series will be focusing on the topic remanufacturing and Circular Economy and take place on February 22.

